Nebula 08 Agenda: “Check what that user was up to, and use it to log into flag08 account.”

All right!!! So basically, what do we have to start with, is a single pcap file format:
1 -rw-r--r-- 1 root root 8302 2011-11-20 21:22 capture.pcap
If working with TCP based protocols it can be very helpful to see the data from a TCP stream in the way that the application layer sees it.
Without doubts Wireshark is a wounderful tool (nonetheless, we aren’t able to use X11-server on Nebula VM. Actually, all is possible =) but that’s definitely is not the best way). It worth to notice that there’s also exist console version called tshark but unfortunately, attempt to setup it on VM due to some failures was unsuccessful. That’s why I had to use what was at hand, in particular tcpflow:
1 level08@nebula:/home/flag08$ tcpflow -cer ./capture.pcap
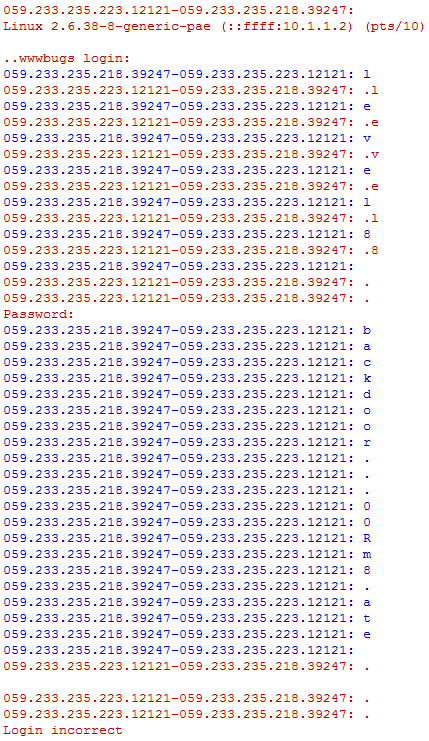
Blue color indicates client to server flow and the red one is server to client. The default behavior in case of printing to file/console is converting all non-printable characters to the “.” character. We have four dots in the password, let’s not guessing but making clear for sure what it exactly is by using wireshark (cannot escape from fate) on the outer host.
Firstly need to pass this instance file out and netcat will help in this.
1 level08@nebula:/home/flag08$ nc -l 8888 < ./capture.pcap
2 # And then on the outer host:
3 nobody@home$ wget -O capture.pcap 192.168.56.102:8888
Secondly, check out on the wireshark:

If grab the ASCII table it appears that “7F” hex represents delete and “0D” - carriage return symbols respectively. The final note as conclusion, after applying “DEL”, the passphrase (flag08 account) becomes - “backd00Rmate”. Hell yeah (òÓ,)_\,,/ !

 "
"




